Honest Security: One Year Later
On December 8th, 2020, we published our honest.security guide. Now, exactly one year later, I thought it would be nice to reflect on everything we’ve learned since publishing the guide, how other organizations have reacted to it, and finally, our vision for the future.
As part of this one-year commemoration, I sat down with the fine folks who host the MacAdmins Podcast. This time, it wasn’t just me; Harlie Hardage, a Senior Security Specialist at 1Password, joined me after leading the Kolide roll-out in their organization last year. On the podcast, she discusses 1Password’s approach to building a robust internal security culture in a rapidly growing team and the tools they’ve looked into that have been compatible (and incompatible) with that approach.
1Password is one of the many companies that joined us last year and a terrific example of an organization growing rapidly while trying to maintain a culture that celebrates user-empowered security.
The show really turned out great, and I learned a few things by listening to Harlie talk about her experiences. Give it a listen!
What Is Honest Security?
If you missed it last year, Honest Security is one part guide and another part manifesto that defines a user-first approach to security and IT compliance. It’s not just Kolide’s north star but also an aspirational roadmap. It’s our positive contribution to counterbalance the worrying upward trend of human-hostile cyber security, device management, and workplace surveillance philosophies that we’ve seen reach a fever pitch as organizations adapt to the long-term term prospects of remote work.
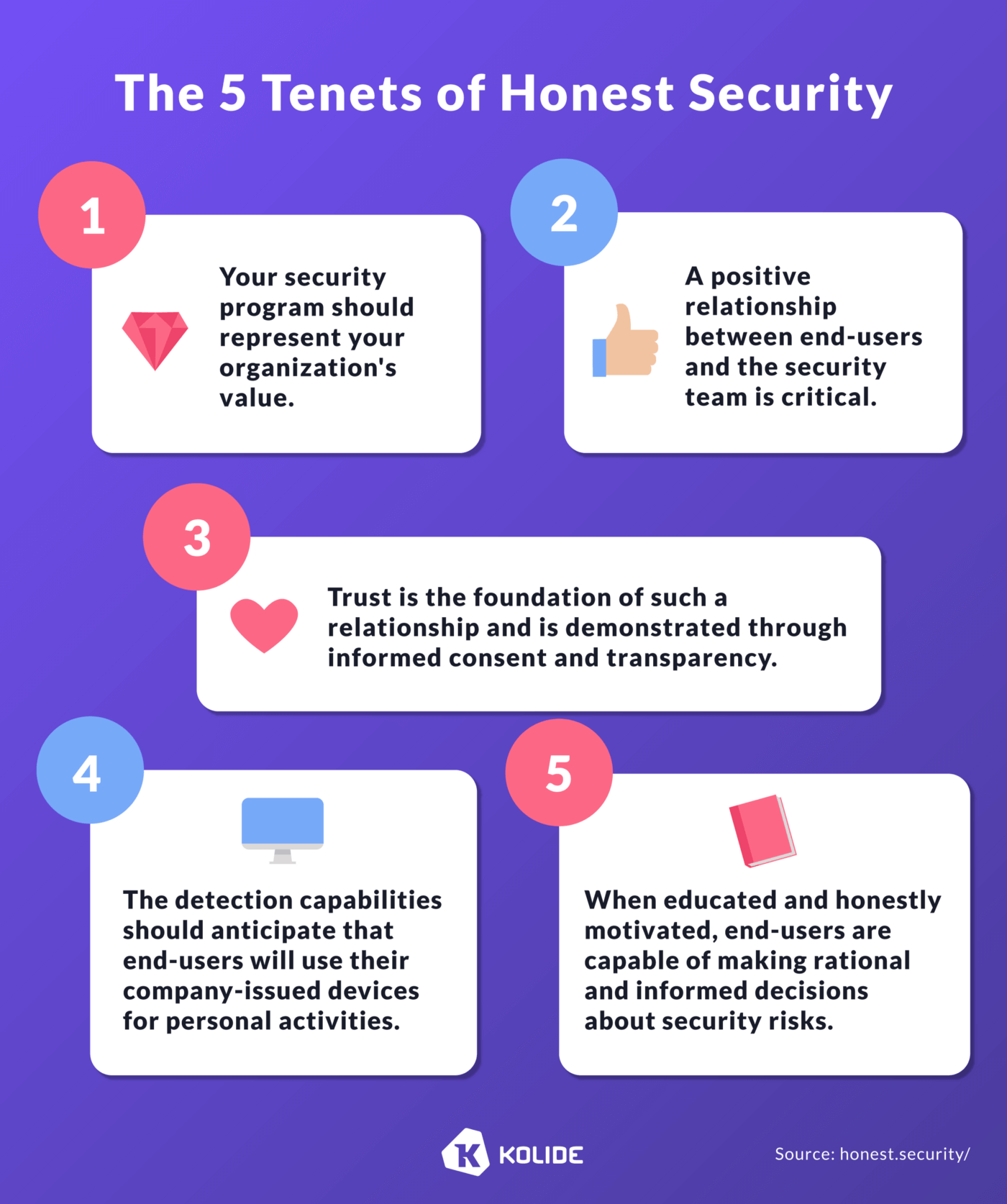
While the entire document is a great read, we distilled down the philosophy to five simple tenets that, a year later, we still stand behind.
What Have We Learned in a Year?
My hope for Honest Security was to identify a population that yearned for a more humanistic approach to IT device management and cyber security. I wasn’t prepared for the sheer avalanche of positive reactions from companies and leaders that we admire. Publishing Honest Security fundamentally changed the trajectory of our business at Kolide, and the outsized response was evidence of a community of IT professionals who longed for tools and philosophies that do not alienate their team from the users that they earnestly wish to support.
Thanks to this influx of growth, we’ve had an opportunity to evolve our understanding of Honest Security as we’ve enabled its adoption at hundreds of new organizations.
While we plan to update our Honest Security guide in 2022, we wanted to share here on the anniversary some of the key insights we learned from putting Honest Security into practice.
The Importance of Radical Transparency
In the Honest Security guide, we discuss how important it is to collect ground truth with honesty and transparency. To us, transparency means end-users can independently understand how their underlying system works without needing to ask a human being or being a technology expert.
In the guide, we use Kolide’s Privacy Center as an example of what an ideal experience might look like. Since then, we’ve completely overhauled it based on the feedback we’ve received directly from end-users from hundreds of customers. Here’s a quick video that explains this overhaul.
Some additional improvements included:
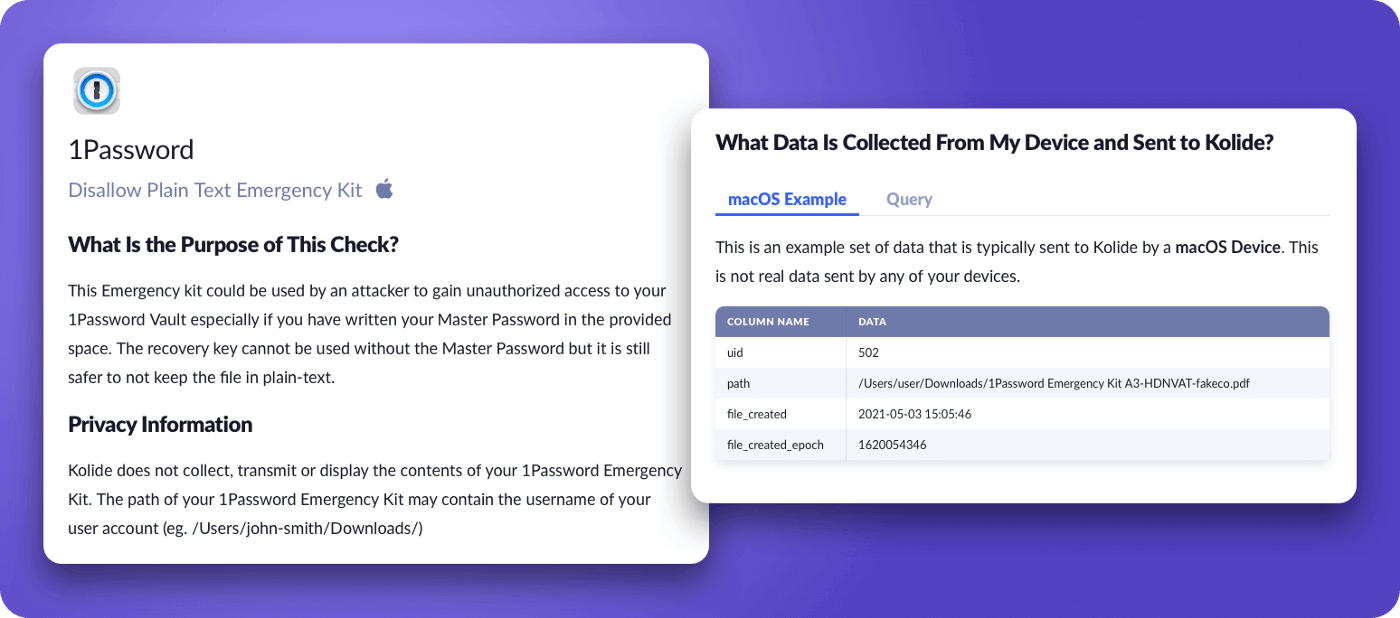
Creating some of the most detailed and end-user accessible documentation about every piece of information Kolide may collect on a device (even devices you may not have enrolled yet)
The Importance of Balancing Data Collection Drawbacks With Benefits
We learned that when our customers achieve transparency, they need the tools to address the inevitable questions and concerns that can come up. For example, Kolide collects data about a device’s browser extensions by default. Perhaps after learning this, end-users may not feel comfortable sharing that information, and upon reflection, the IT team may also agree that the benefits provided by data collection do not outweigh the privacy concerns. To ensure Kolide collects the exact amount of data to empower each organization’s specific objectives, we had to build an experience that allows you to turn off certain types of data collection in Kolide and clearly explains the tradeoffs of doing so.
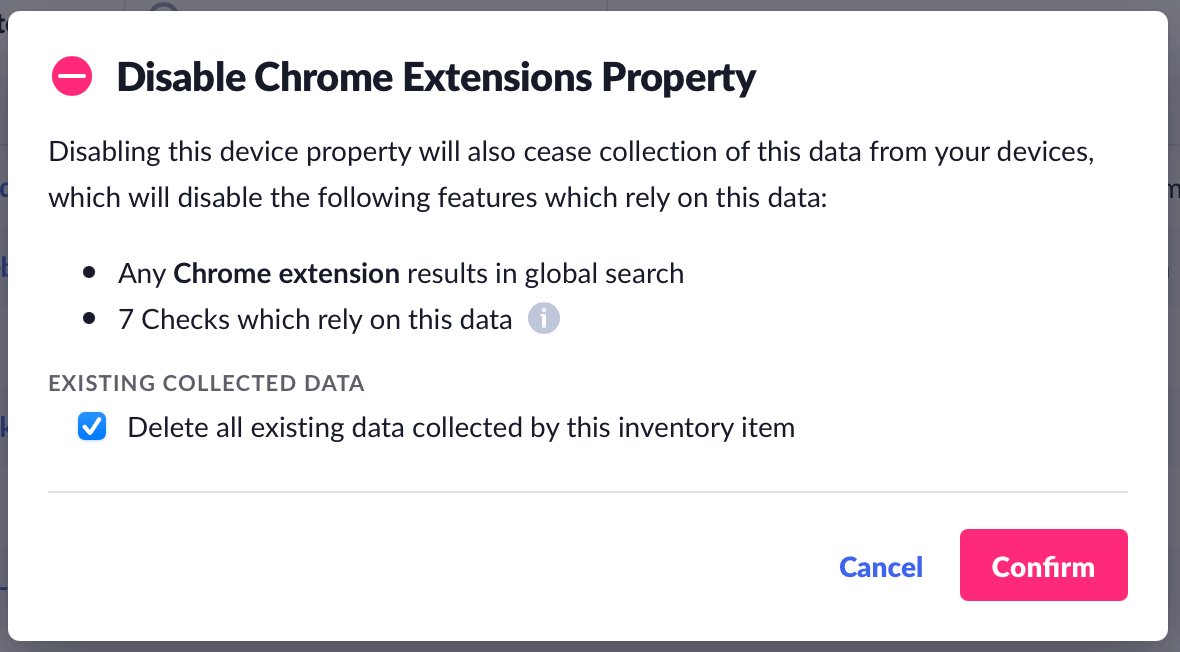
While the screen above is simple to read and understand, it requires us to extensively map every piece of information Kolide is capable of collecting with the precise benefits it affords. This process ensures that each piece of information we collect in the platform going forward is part of a robust discussion which acknowledges the tradeoffs between privacy and security and ultimately puts the final decision in the hands of our customers.
What Informed Consent Looks Like Post-Install
In the Honest Security guide, we talk about informed consent through the eyes of our Slack-based onboarding process. This is a process where end-users actually install Kolide’s endpoint agent after they have an opportunity to understand what Kolide does and what data it collects.
However, when we designed our Lost Mode feature, we leveled up our understanding of what a continuous informed consent process looks like and built it in as a process we will use for all extremely sensitive device actions. In my Building Honest Software talk at RubyConf this year, I break down the anatomy of what proper informed consent looks like in software that practices honesty as a core tenet.
This UX breakthrough has let us continue to deliver high-value features without compromising our commitments to transparency and privacy. We plan to leverage this overall workflow for more features that require sensitive data and share our improvements to this consent-based process.
What Is Next For Honest Security & Kolide
There is one section of the Honest Security guide that Kolide still has yet to reach. It’s called Generating Predictable Consequences. In this section, we acknowledge and discuss the realities of relying on fallible human beings to ensure the ongoing security compliance of their devices. We ultimately recommend creating proportionate and predictable consequences to devices not meeting a minimum standard.
This concept of gating access based on a device’s security state is not new. Zero-Trust and Beyond Corp are similar methodologies that enable this exact use case. That said, the existing tools lack two things: an emphasis on user education and a much more nuanced and progressive approach to eventually arriving at effective consequences (like access revocation). Many of these solutions work silently in the background, removing end-users from critical resources with little to no warning, and without any paths to self-resolve the problem without opening a support ticket.
Some of our most technical customers have stunned us with their homegrown efforts to build this nuanced approach on our existing API. One has even open-sourced their efforts. As soon as these efforts rolled out, Kolide instantly became an essential piece of their endpoint visibility and access control story.
With that said, we believe this shouldn’t be something each one of our customers has to build themselves. If there is a singular focus for our product in 2022, it’s releasing a thoughtful and nuanced way to approach this final piece of the Honest Security Guide that doesn’t require programming knowledge or a specific stack of SSO or VPN providers.
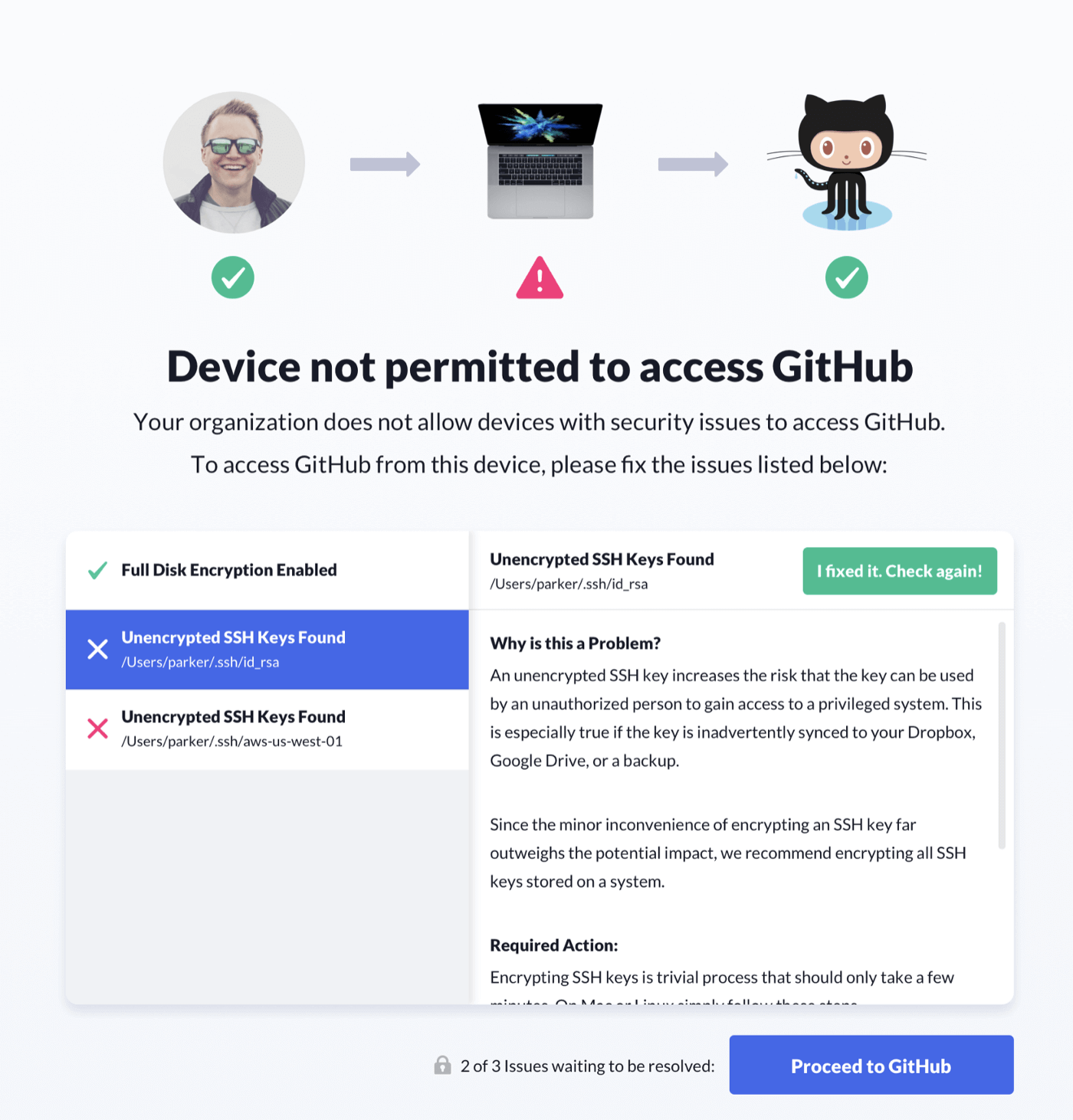
As with everything we do with Honest Security, we expect to tread new ground and learn a lot about how to implement truly predictable and proportion consequences. Once we collect these thoughts, expect a robust and comprehensive update to our Honest Security guide.
Thank you everyone for such an incredible year and for your support of our Honest Security mission. We can’t wait to see how this community and movement evolve in 2022.
Additional Reading/Listening
Listen to the “Honest Security: One Year Later” episode on MacAdmins Podcast featuring Jason Meller (Kolide) and Harlie Hardage (1Password)
Learn more about Harlie on her website