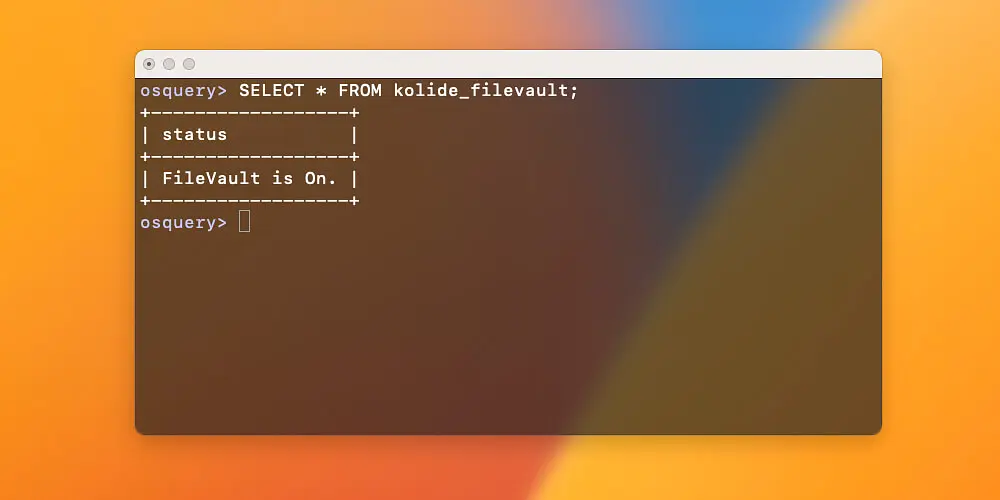
Featured
Buying Kolide vs Building Your Own Osquery Solution
When you're having the "build vs buy" conversation, here's how to compare
Kolide vs in-house osquery.
Read More

Tutorials
The File Table: Osquery's Secret Weapon

Tutorials
How to Write a New Osquery Table
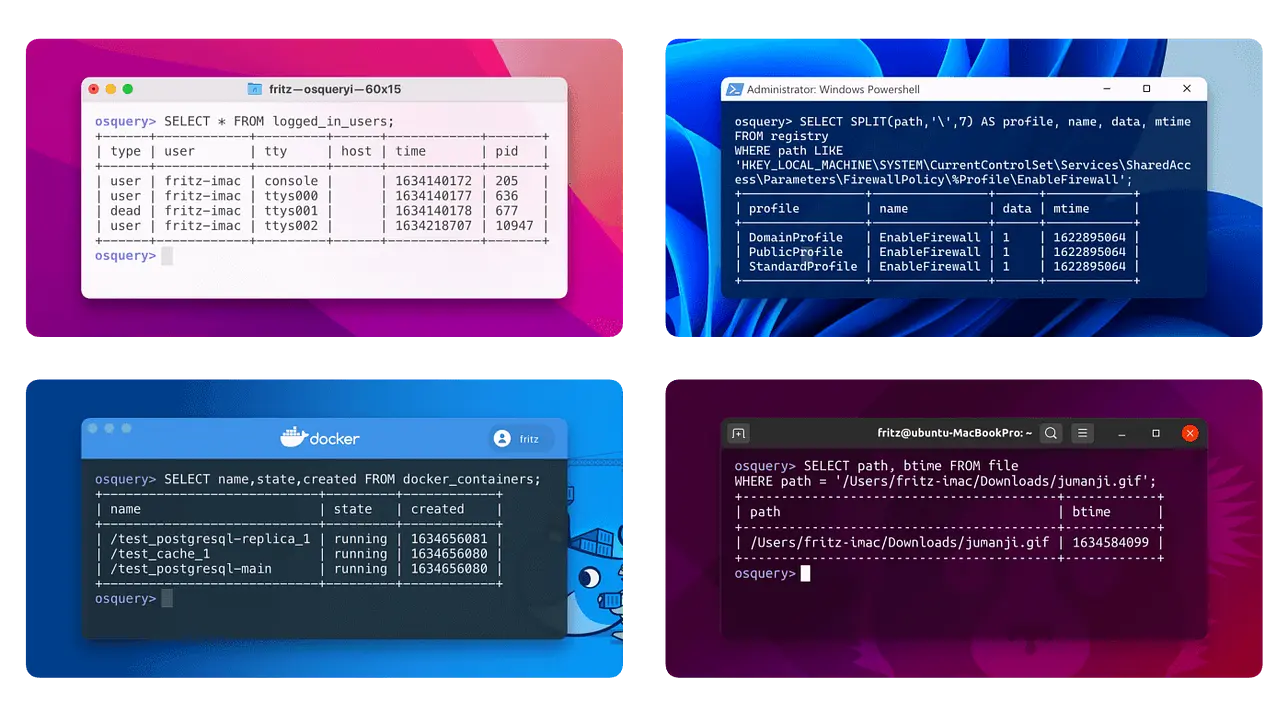
Tutorials
How to Deal With Dates and Times in Osquery

Deep Dives
Why You Can't Trust Your NULLs in Osquery

Tutorials
How to Find a Mac's Manufacture Date Using Osquery

Inside Kolide
How Kolide Built Its macOS Screenlock Check
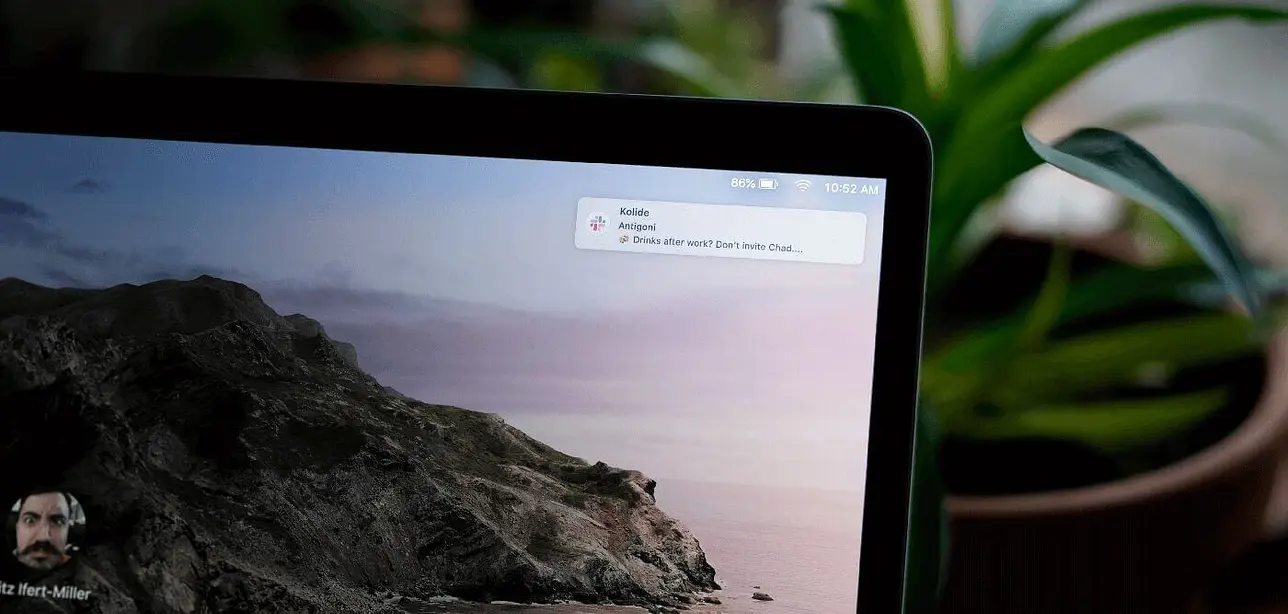
Deep Dives
Are Your Employees Slack Messages Leaking While Their Screen Is Locked?
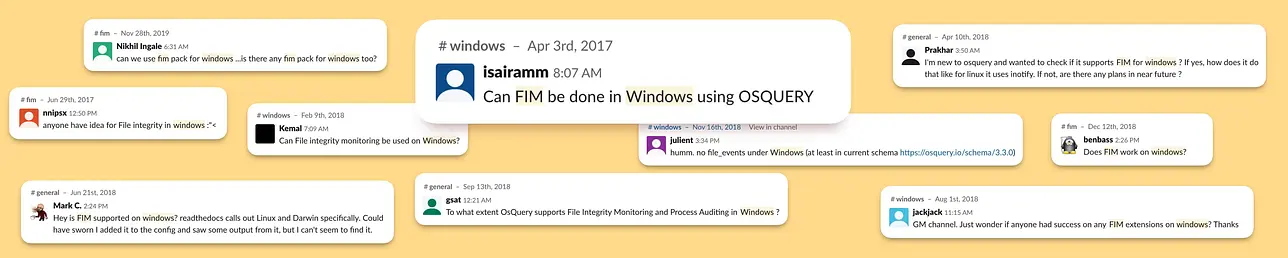
Tutorials
How to Set up Windows File Integrity Monitoring Using Osquery and Kolide
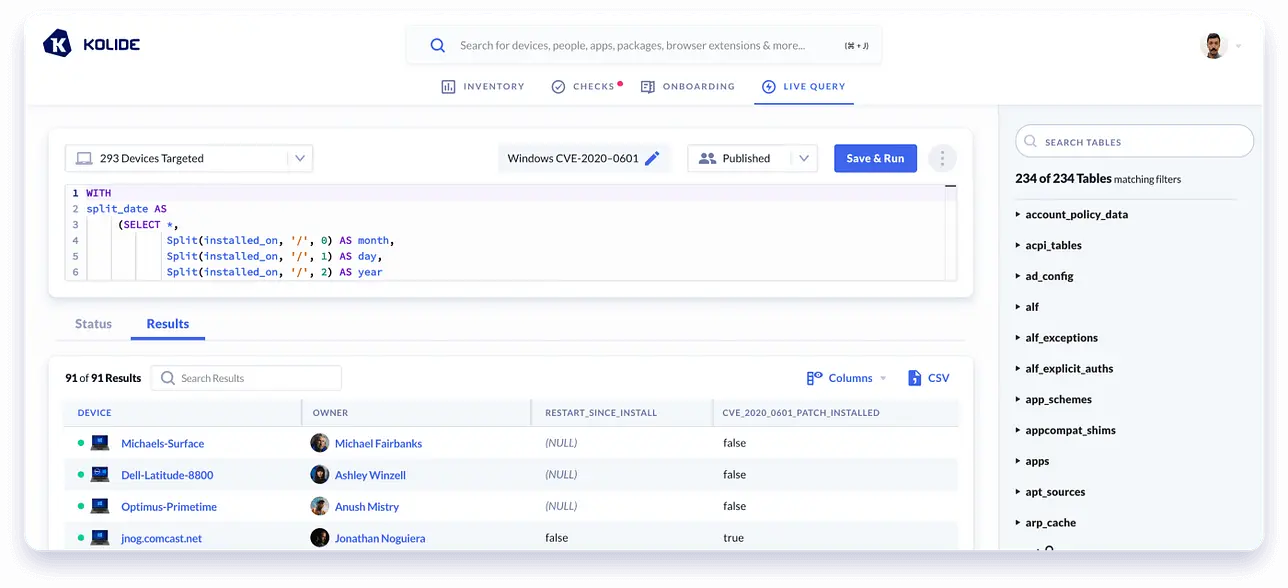
Tutorials
How to Find and Fix CVE-2020–0601 Using Osquery and Kolide

Tutorials
How to Read Nested Complex Plists in Osquery

Deep Dives
macOS Catalina & Osquery

Deep Dives
Zoom Webcam Hijacking — Are Your Users Vulnerable?